🔥 Our new AI Assistant, Navigator, is now available for beta testing.
🔥 Subscribe to Our Monthly Security Digest Newsletter
Sign Me Up
Sign Me Up
- Products
SD ELEMENTS
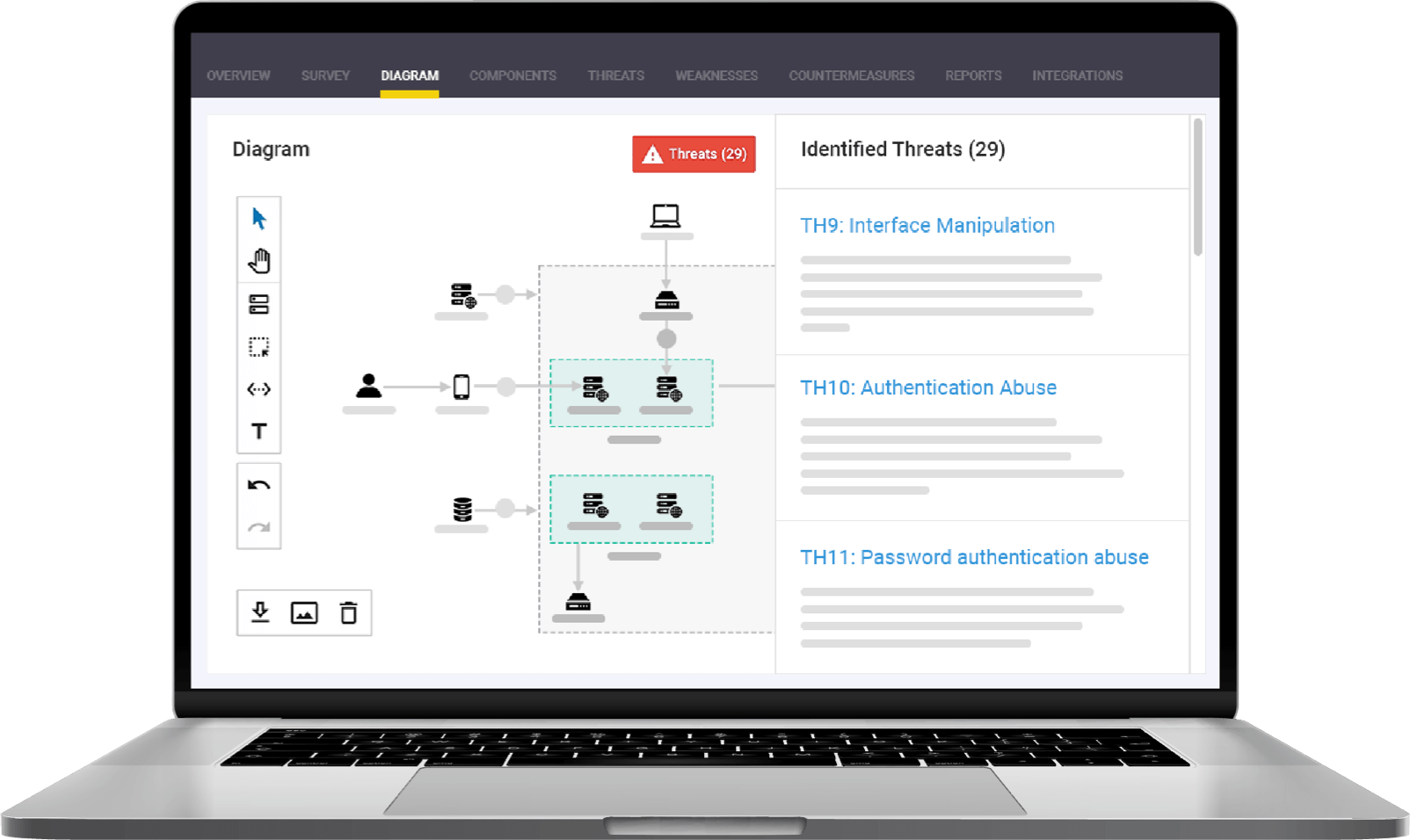
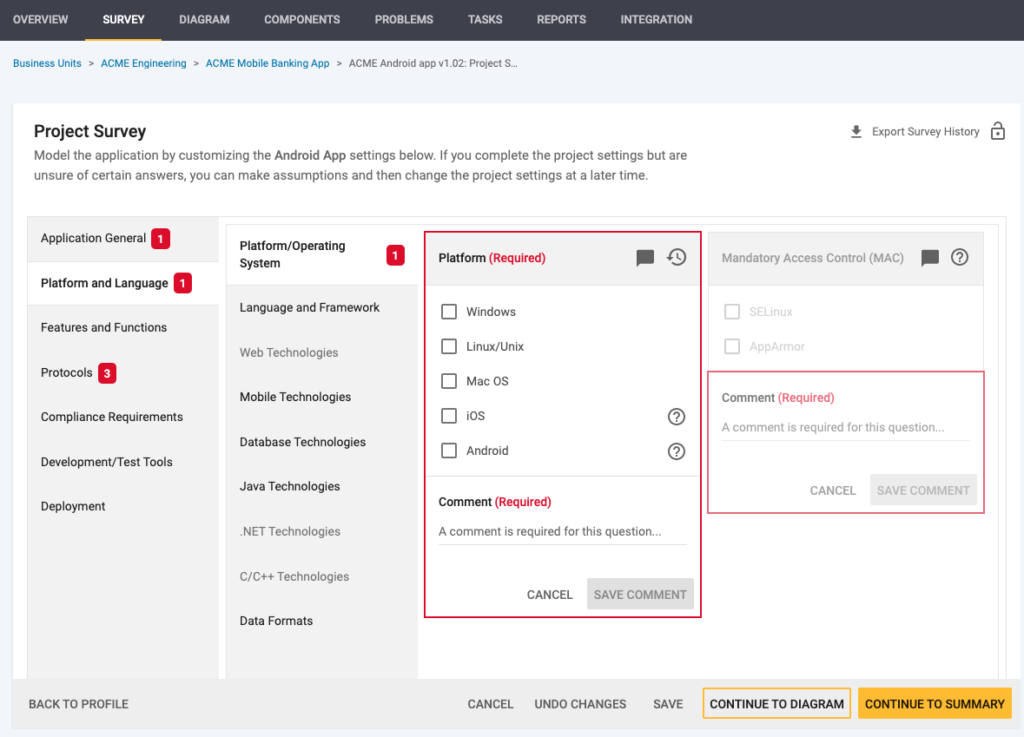
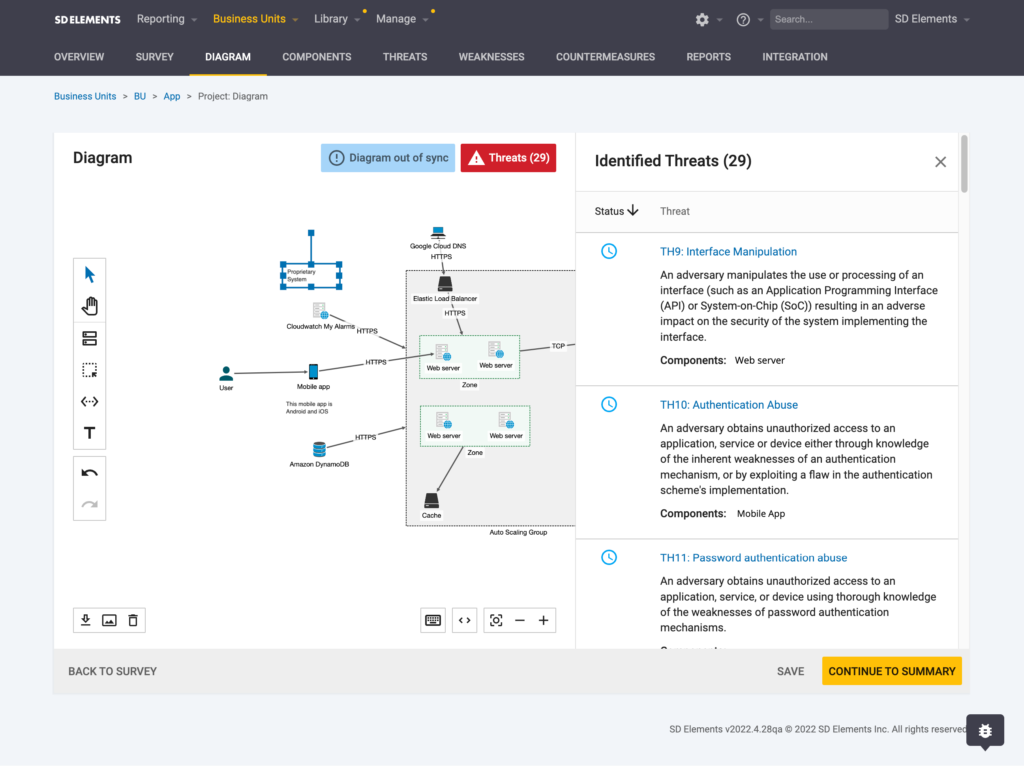
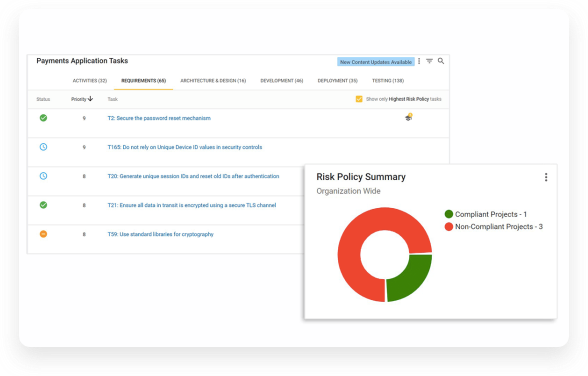
Build with security and compliance from the beginning of the development process, preventing delays and rework.SD BLUEPRINT
Automate threat model generation, management of security requirements, and adherence to regulatory compliance.APPLICATION SECURITY TRAINING
Role based application security training for all your team’s compliance, secure coding, and deployment needs.
Security by Design
Discover comprehensive guides and expert insights, designed to empower your organization with knowledge and tools for a security-first approach. - Solutions
USE CASES

Product Tours
Select an interactive product tour to delve into SD Elements, SD Blueprint, and Application Security Training.
Featured Article
SOC 2 compliance is a framework for managing data based on five trust service principles. - Resources
MEDIA
- Company

SC in the News
Stay up-to-date with our latest news, including insights on the latest developments in application security. - Product Tours
- Book Demo
- Mobile Only