The Defense Industrial Base (DIB) is comprised of thousands of organizations that design, produce, deliver, and maintain military weapons systems, subsystems, and components for the U.S. Department of Defense (DoD). Like many complex systems, the DIB includes primary contractors and third-party subcontractors producing parts, software, and complete systems. This can include government contractors, universities, service providers, and manufacturers.
U.S. federal government agencies are under more pressure than ever before to modernize their IT systems and consistently deliver better services at lower costs. They also must comply with increasingly stringent cybersecurity requirements to obtain Authority to Operate (ATO). Rapidly developing and deploying secure software in a way that meets ATO requirements, especially within environments where software project volume, complexity, and delivery pace are high and security expertise is in short supply. This makes attaining ATO or maintaining continuous ATO (cATO) extremely difficult. A key part of this is protecting Controlled Unclassified Information.
Protecting Controlled Unclassified Information
To fulfill contracts, it is necessary for the DoD to share sensitive information with its contractors, including classified and Controlled Unclassified Information (CUI). CUI is defined as “any information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that is required to be protected under law, regulation, or Government-wide policy.” CUI is much more common than most organizations realize. Even if a company is only a 3rd party supplier to a government contractor, flow-down terms and specifications can be considered CUI. This can include:
- Personally Identifiable Information (PII)
- Sensitive Personally Identifiable Information (SPII)
- Proprietary Business Information (PBI) or currently known within EPA as Confidential Business Information (CBI)
- Unclassified Controlled Technical Information (UCTI)
- Sensitive but Unclassified (SBU)
- For Official Use Only (FOUO)
- Law Enforcement Sensitive (LES)
Cybersecurity Maturity Model Certification (CMMC)
To ensure that DIB contractors establish and maintain effective cybersecurity practices for CUI, the DoD published the Cybersecurity Maturity Model Certification (CMMC) program in 2020. CMMC is a framework that allows the DoD to measure the maturity of an organization’s cybersecurity practices. Rather than build redundant standards, the DoD modeled CMMC on several existing cybersecurity standards, including NIST 800-53, NIST 800-171, The Defense Federal Acquisition Regulation Supplement (DFARS), and International Traffic in Arms Regulations (ITAR).
CMMC 2.0
After receiving agency and contractor feedback about the original standards, the DoD announced CMMC 2.0 in a November 2021 update to streamline requirements. CMMC 2.0 reduced CMMC 1.0’s five tiers of maturity to three: Foundational, Advanced, and Expert. The level of compliance required by an organization varies with the form and caliber of CUI that they work with. A comparison of requirements for CMMC and CMMC 2.0 appears below.
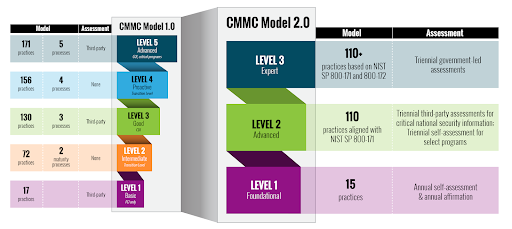
As shown, CMMC 2.0 uses three progressively sophisticated levels, depending on the type of information being managed:
- CMMC Level 1 (Foundational): Level 1. covers only Federal Contract Information (FCI), information that requires protection but is not critical to national security. It is expected to cover most federal contracts and does not include Commercial Off the Shelf software. Level 1 includes 17 security practices derived from FAR Clause 52.204-21: Basic Safeguarding of Covered Contractor Information Systems. Organizations subject to Level 1 controls must provide annual self-assessments and attestations.
- CMMC Level 2 (Advanced) is a requirement for companies with CUI. Level 2 certification requires compliance with the practices detailed in NIST SP 800-171: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations. It requires triennial third-party assessments for prioritized acquisitions and annual self-assessments for non-prioritized acquisitions.
- CMMC Level 3 (Expert) covers organizations in the highest priority programs with CUI. CMMC Level 3 will require compliance with controls detailed in NIST SP 800-171 as well as a subset of security practices from NIST SP 800-172: Enhanced Security Requirements for Protecting Controlled Unclassified Information: A Supplement to NIST Special Publication 800-171. Level 3 certification will require triennial assessments by the DoD.
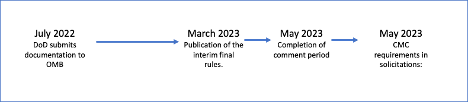
CMMC 2.0 Timeline
CMMC 2.0 will not be a contractual requirement until the Office of Management and Budget (OMB) completes rulemaking. While CMMC has experienced some delays, and more may be coming. Last summer the National Law Review anticipated the OMB would issue interim final rules by March 2023. This would mean, CMMC requirements could begin appearing in solicitations as early as 60 days later.
How to Prepare for CMMC
There are several steps organizations can take to prepare for CMC requirements in DoD solicitations. These include:
- Understand your CMMC certification level: Work with your partners to understand the classification of the data you access. While Level 1 controls are required of all organizations, you may need time to comply with the practices in in NIST SP 800-171 and NIST SP 800-172.
- Operationalize compliance: Most organizations audit compliance requirements manually using spreadsheets and shared documents. These are difficult to track for those responsible for complying with the 100+ standards required in a Level 2 or 3 requirement. Providing a centralized platform simplifies communicating, tracking, and auditing controls.
- Threat modeling can help: Threat modeling anticipates threats and assigns actionable controls to development, security, and operational personnel. An automated platform can also map regulatory requirements for CMMC like NIST SP 800-171, NIST SP 800-172, and others to appropriate controls and provide a single resource for all stakeholders to track compliance.
Next Steps
The CMMC is an important program that has made significant progress in protecting government and defense contractors from cyber threats. While there have been challenges and obstacles along the way, the future of the CMMC looks bright and it is likely to continue to play a crucial role in promoting good cybersecurity practices in the government and defense sectors.
To learn more about how SD Elements can provide your organization with a proactive approach to identifying, tracking, and auditing requirements under CMMC and achieving ATO and cATO, check out our resources here.









