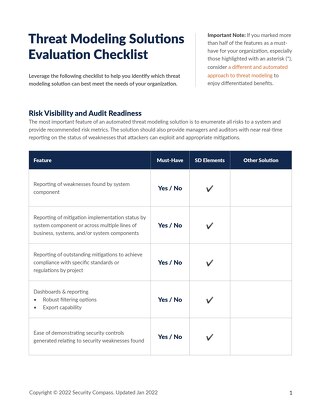
Use this checklist to identify which threat modeling solution meets the needs of your organization.
Threat Modeling Solutions Evaluation Checklist
🔥 Subscribe to Our Monthly Security Digest Newsletter



MEDIA


Use this checklist to identify which threat modeling solution meets the needs of your organization.