In an era where data breaches are costly and can deeply damage a company’s reputation, understanding the intricacies of compliance frameworks is not just beneficial—it’s imperative. SOC 2 compliance is a key differentiator for businesses prioritizing data security and privacy, reassuring clients of their commitment to safeguarding sensitive information.
This comparative guide delves into the specifics of SOC 2 Type 1 and Type 2 audits, elucidating the differences and helping you determine which is most aligned with your business needs.
As we navigate the nuances of these standards, businesses will gather the insights needed to implement robust security measures, demonstrating their unwavering dedication to data protection to clients and partners alike.
What Is SOC 2?
SOC 2 is a data management framework that outlines how organizations should handle customer information based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 is specifically designed for service providers storing customer data in the cloud. This framework is pivotal in assuring clients that their information is protected against unauthorized access and privacy breaches.
In performing a SOC 2 audit, organizations must demonstrate adherence to one or more of the trust service criteria relevant to their operations and business practices. Through these audits, businesses protect customer data, build trust, and maintain their reputation in an increasingly security-conscious market.
Understanding SOC 2 Type 1
SOC 2 Type 1 is an audit that assesses an organization’s systems and the suitability of its design to meet relevant trust principles as of a specified date.
A Type 1 audit is a snapshot in time that evaluates the design of your data security controls. When auditors come in for SOC 2 Type 1, they want to understand whether your company’s system design can meet the SOC 2 criteria during the audit. This includes a thorough examination of your policies, procedures, and technologies as they pertain to the AICPA’s trust service criteria.
For companies looking to establish credibility quickly, especially startups or those new to cloud services, the SOC 2 Type 1 report can demonstrate a strong commitment to data security early on.
It’s a crucial first step in the journey toward comprehensive security and compliance, assuring the company and its stakeholders about the system’s design effectiveness as per the trust principles.
When is SOC 2 Type 1 Appropriate?
SOC 2 Type 1 is ideal for businesses seeking to demonstrate their commitment to security controls at a specific time.
Organizations often undertake a Type 1 audit when they are in the initial stages of implementing their compliance strategies or when they need to validate the design of their controls quickly.
This could be due to client requests, contractual obligations, or as part of a strategic move to get ahead in the market. SOC 2 Type 1 proves that an organization has established systems properly designed to protect client data according to the SOC 2 criteria.
Furthermore, it is a particularly useful tool for companies planning to undergo a more rigorous SOC 2 Type 2 audit. It can act as a precursor, allowing companies to identify and address any potential design issues before a Type 2 audit assesses the operational effectiveness of these controls over time.
Choosing SOC 2 Type 1 is a strategic decision that can lead to smoother compliance processes in the future.
What is SOC 2 Type 2 Audit?
SOC 2 Type 2 is an audit that assesses the operational effectiveness of an organization’s controls over a defined period.
A Type 1 audit focuses on the suitability of control design at a single point in time. In contrast, a Type 2 audit examines how well those controls operate over a duration, typically covering 3-12 months. The objective is to provide assurance that the company’s security practices are designed effectively and consistently applied over the audit period.
Auditors will review evidence of how the controls have been functioning, which may involve inspecting system logs, records, and other documentation demonstrating the controls in action.
SOC 2 Type 2 requires a sustained effort to maintain compliance, representing a more in-depth demonstration of a company’s commitment to data security and processing integrity. Completing this audit is often seen as a hallmark of reliability and a higher standard of trust for customers and stakeholders.
When is SOC 2 Type 2 Necessary?
SOC 2 Type 2 is necessary for businesses that must prove their security controls’ effectiveness over time.
Companies that handle sensitive client data continuously find it essential to undergo a Type 2 audit. This reassures clients of their commitment to long-term security and operational integrity. It becomes particularly vital for service providers subject to continuous and rigorous scrutiny from their clients or operating in industries where data security is paramount.
The need for a SOC 2 Type 2 audit may also stem from regulatory requirements, client contracts, or market pressures, which demand higher transparency and assurance regarding data security practices.
This type of audit is also seen as a competitive advantage, as it signals to potential clients that the organization is compliant with industry standards and proactive about protecting stakeholder interests with effective security measures.
Choosing to undergo a SOC 2 Type 2 audit showcases a company’s dedication to maintaining robust, secure operations over the long term.
Key Differences between SOC 2 Type 1 and Type 2
The main difference between SOC 2 Type 1 and Type 2 is the audit duration and the control effectiveness assessment over time.
To delineate further, SOC 2 Type 1 is akin to photographing; it captures how the controls are designed at a specific moment. In contrast, SOC 2 Type 2 is more like a documentary, providing a dynamic, in-depth view of how those controls perform and endure over a period that’s typically no less than 3-12 months.
Let’s compare the two:
|
|
Type 1 |
Type 2 |
|
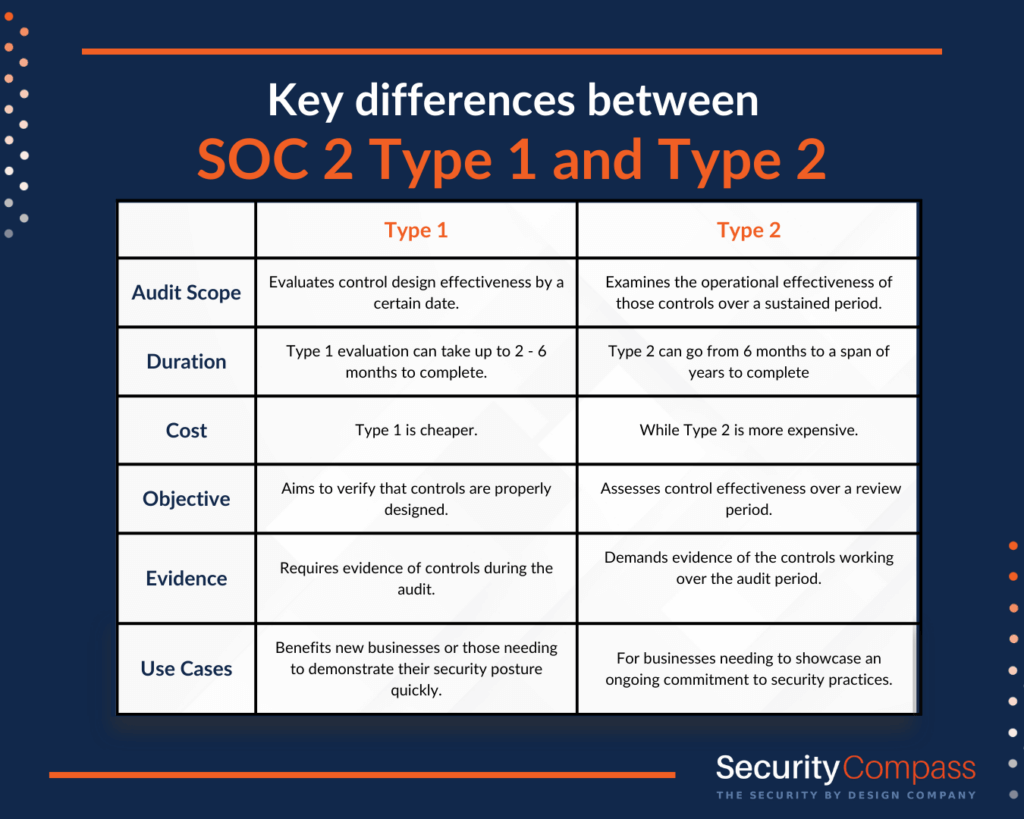
Audit Scope |
Type 1 evaluates control design effectiveness by a certain date. | Type 2 examines the operational effectiveness of those controls over a sustained period (3,6,9 and 12 months). |
|
Duration |
Type 1 evaluation can take up to 2 – 6 months to complete | Type 2 can go from 6 months to a span of years to complete |
|
Cost |
Cheap | More expensive |
|
Objective |
Type 1 aims to verify that controls are properly designed. | Type 2 assesses control effectiveness over a review period. |
|
Evidence |
Type 1 requires evidence of controls during the audit | Type 2 demands evidence of the controls working over the audit period. |
|
Use Cases |
Type 1 benefits new businesses or those needing to demonstrate their security posture quickly. | Type 2 is for businesses needing to showcase an ongoing commitment to security practices. |
While both audits validate an organization’s dedication to protecting client data, they cater to different stages of compliance maturity and serve different purposes depending on the business objectives.
Choosing the Right SOC 2 Audit for Your Business
Choosing between SOC 2 Type 1 and Type 2 should be a strategic decision based on your business’s specific context, the maturity of your security program, and your customers’ expectations. Factors to consider include:
1. Current Stage of Your Security Program
If you’re developing your security practices early or need to validate your system design quickly, Type 1 may be appropriate. If your security controls are well-established and you’ve been in operation for some time, Type 2 can provide a more comprehensive validation.
2. Customer and Market Demand
Depending on your industry and the sensitivity of the data you handle, customers may mandate a Type 2 audit as part of their vendor risk management processes. Type 2 audits are often seen as more rigorous, and passing one can open doors to partnerships with larger enterprises that require a proven track record of security compliance.
3. Regulatory Requirements
Certain industries may have specific regulatory mandates requiring a SOC 2 Type 2 audit. Understanding these requirements is crucial in deciding which audit your business should undergo.
4. Long-term Business Goals
Consider your organization’s vision. Conducting a SOC 2 Type 2 audit demonstrates an ongoing commitment to security that helps retain current customers and attract new ones.
Ultimately, the decision on which SOC 2 audit to choose should align with your company’s need to build trust with stakeholders and ensure the continual protection of customer data.
Security Compass can facilitate a deeper understanding of these requirements to ensure you are prepared for the audit process and can achieve SOC 2 compliance irrespective of the type chosen.
Preparing for SOC 2 Audits

Preparing for a SOC 2 audit, whether Type 1 or Type 2, involves a holistic approach to reviewing and enhancing your organization’s security posture.
To prepare for a SOC 2 audit, businesses should focus on internal preparation, thorough documentation, and employee training. Take proactive steps by:
Conducting a thorough assessment of your current controls against SOC 2 requirements.
- Developing or refining policies and procedures that align with the Trust Service Criteria.
- Implementing necessary changes ensures your systems and controls are SOC 2 compliant.
- Documenting everything meticulously, as auditors will require detailed proof of your controls and policies.
- Engaging in employee training ensures all staff members understand their role in maintaining SOC 2 compliance.
Conclusion
As data security becomes ever more critical in the digital age, SOC 2 compliance emerges as a fundamental benchmark for businesses looking to protect client information and establish trust.
The choice between SOC 2 Type 1 and Type 2 audits represents more than a mere procedural decision—it’s a strategic move that reflects a company’s dedication to rigorous data security standards. This guide has laid out the variances and uses of both audits, empowering businesses to make an informed decision that resonates with their specific security, business, and customer requirements.
Remember, whether it’s a Type 1 audit that provides quick verification of your controls or a Type 2 audit that offers in-depth insight into your security’s effectiveness over time, the end goal is to ensure customer data’s confidentiality, integrity, and availability.
Taking action toward SOC 2 compliance fortifies your security posture and bolsters your credibility in a competitive marketplace. Security Compass remains committed to aiding organizations on their path to compliance, ensuring that the journey is as seamless and effective as possible.
Additional Resources:
For further information on SOC 2 compliance or to delve deeper into the differences between SOC 2 Type 1 and Type 2 audits, you can explore the following resources:
- The AICPA’s Guide to SOC 2 Reports: https://www.aicpa.org
Embarking on the SOC 2 audit path is a proactive step toward securing your organization’s future. By choosing the right type of audit and preparing thoroughly, your business is well on its way to demonstrating its unwavering commitment to data security and customer trust.









