What’s the last news cycle you remember that did not include a cybersecurity horror story? If you read business news regularly, you are likely learning of this week’s latest cyber breach, breathing a sigh of relief that you were not the victim — at least not this time.
Jim Lewis of the Center for Strategic and International Studies said, “We have a faith-based approach [to cybersecurity], in that we pray every night nothing bad will happen.”
Cybersecurity should no more be a prayer than an afterthought. For developers and executives alike, peace of mind can be achieved by starting the journey early on, adopting proactive approaches that integrate security into software development from the start.
While many experts say the complexity of the shocking attack of SolarWinds represents a new frontier for cybersecurity, it also is the latest episode in a continuing game known as the “side-door hack” that some companies are not prepared to defend against. Cyber attacks via malicious code planted in a trusted vendor’s software have been done repeatedly and successfully.
Threat modeling as a proactive and consistent practice in software development is the ounce of prevention that can help prevent such breaches. A relatively small investment up front can save exorbitant amounts of time and money to unravel the damage of such attacks, including to your reputation.
The state of threat modeling
We recently conducted a study to get a better understanding of the current state of threat modeling in mid-sized, and large-sized enterprises, with a specific focus on the challenges organizations face in scaling threat modeling. Individuals directly involved in threat modeling efforts within their organizations provided insights on their companies’ approach as well as gaps and vulnerabilities.
The most pressing issue uncovered by the study was the growing priority of threat modeling for applications that companies build and the desire to automate all or most of these efforts. Over 60 percent of organizations believe that all aspects of their organization’s threat modeling could be fully automated, yet only 28 percent have reached that threshold.
Traditional threat modeling practices can be slow, causing tension in organizations that are trying to get their applications to market quickly. Perhaps because of these competing interests, only 25 percent of survey participants indicate their organizations conduct threat modeling during the early phases of software development. However, we all know from the news headlines that neglecting threat modeling and security by design principles in the early stages of development leads to more onerous vulnerabilities later. When it comes to cybersecurity, it makes no sense to be penny-wise and pound-foolish. Bridging this cost and effort gap, all respondents favored automation.
What holds companies back from integrating threat modeling early?
Over half of the respondents reported issues when trying to integrate this essential process into their existing technologies, with 41 percent expressing that it takes too long. These shortcomings contributed to the finding that less than half of these organizations feel very prepared for critical cybersecurity threats. There is a clear need for more scalability and automation in threat modeling to balance rapid software development with secure software development.
A recent MIT article suggests that while it is common for software developers to offer products with very specific selling points, including functionality feature sets and speed-to-market options, cybersecurity often is not among the attributes touted.
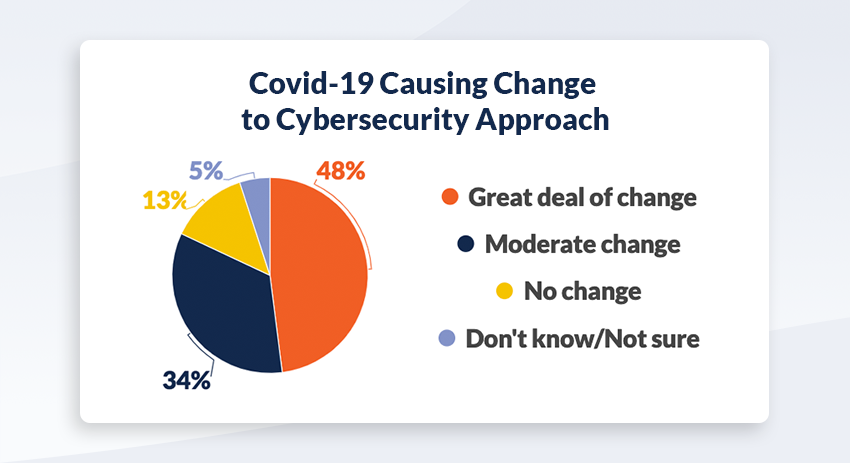
Supply chains may be particularly vulnerable, with more than 84 percent of organizations in our survey reporting cybersecurity changes because of supply chain vulnerability. However, 31 percent conduct threat modeling on less than half the applications they develop that are associated with their supply chain. Authors of a recent research paper published in the Harvard Business Review argued that when companies buy digital products, they expect them to be secure and that in most cases, they do not test for vulnerabilities through the digital supply chain. They may not even have adequate processes or tools to do so. The paper concludes that as a result, incidents of supply chain cyber attacks that exploit weaknesses within the digital supply chain to break into organizations’ internal networks are on the rise.
Marrying business goals with security goals is the key to success when it comes to cybersecurity. Software is being used in almost every aspect of everyday life, making it essential for organizations to perform timely threat modeling on the applications they develop and deploy.
Threat modeling ensures that vulnerabilities are recognized and remediated before they become a problem. Companies have to self-assess, identify areas where they can automate, and improve their existing approach to threat modeling, to ultimately improve their overall security posture. Business leaders who make this a selling point, are ultimately going to win both in terms of time to market and the security of their applications.