Application Security Is in the News Again
The importance of secure software to organizations becomes clearer each year. Web-facing software that manages sensitive data is an attractive target for malicious hackers. It can provide a pathway to data, including personally identifiable information (PII) that can be used for identity theft, personal health information (PHI) that can be leveraged for insurance fraud, financial data that can allow securities fraud, and intellectual property and trade secrets valued by competitors and nation-states.
The attacks take several forms. Criminals can take advantage of vulnerabilities in popular open-source projects to gain access to systems. This was the attack vector in the 2017 breach at the consumer credit reporting agency Equifax that exposed personal data of 143 million consumers. Similar vulnerabilities in commercial software offer similar access.
No organization is “under the radar” for criminals. Supply chain security is necessary in today’s interconnected world. A weakness in a vendor’s or partner’s security profile can introduce risk to its customers. The 2022 Verizon Data Breach Investigations Report showed that 62% of system intrusion incidents came through partners and other third parties. These include the 2020 SolarWinds Breach and this year’s vulnerability in Progress Software’s MOVEit file transfer software. The latter attack (attributed to Russia) resulted in the exposure of hundreds of thousands of emails from the Departments of Defense and Justice, personal data on over 800,000 Sutter Health patients, and nearly the entire population of the State of Maine.
Traditional Approaches to Application Security Present Challenges
The demand for more secure applications has never been higher. Unfortunately, traditional approaches to building secure software simply do not work in today’s environment. The “find and fix” approach requires teams to test software late in the development process using static and dynamic analysis tools to identify vulnerabilities. Here are a few key challenges that exist for Application Security professionals and development organizations:
- Developers are not trained in security development: Security is usually not part of the functional specification of software. Indeed, software development teams have always been measured on a functional basis. If they delivered features on time, they were doing their jobs right. Security was never considered until 20 years ago, and secure coding is still rarely taught in computer science programs.
- Scalability: Both classes of scanning tools can produce thousands of results, the majority of which are often false positives or “informational” alerts. Discerning true positives from false positives can be arduous; examining a single finding requires 10 minutes on average. In other words, triaging only 240 issues requires 40 hours — a workweek — of effort. Few organizations have sufficient resources for this exercise and instead, simply assign all findings to development.
- Scarce security resources: According to the ISC2 2023 Cybersecurity Workforce Study, there are over 4 million unfilled cybersecurity positions, including more than 500,000 in North America and over 340,000 in both Latin America and Europe. Three-quarters of cybersecurity professionals perceive the present threat environment as the most demanding in the last half-decade. At the same time, just over half, at 52 percent, are confident that their organization has the necessary tools and personnel to address cyber incidents in the upcoming years. The “find and fix” approach requires extensive security expertise. Static analysis tools can be difficult to deploy and manage. Dynamic analysis requires a trained security resource and a staging environment. Providing guidance on the proper method for remediating vulnerabilities strains already scarce application security resources.
- DevSecOps can complicate security: Development teams often face tight deadlines and resource constraints, prioritizing the delivery of features more quickly than ever. Rapid development methodologies like agile, DevSecOps, and Continuous Integration/Continuous Deployment (CI/CD) have grown in popularity. More rapid development and deployment methods are incompatible with many traditional security testing tools that require hours or days to complete. Testing for security after a build lengthens remediation efforts. Unfortunately, pressure to provide features previously promised to customers and stakeholders means many of these vulnerabilities may not be remediated prior to releasing the software.
Security by Design Mitigates Risk
A better approach is to build security into applications from the very beginning of the development process. Security by Design is an approach endorsed by CISA, the National Security Agency, and the Department of Justice in the United States, along with more than a dozen government agencies across the world, including:
- The Canadian Centre for Cyber Security
- The United Kingdom’s National Cyber Security Centre
- The Organization of American States covering North, Central, and South America
- Germany’s Federal Office for Information Security
- The Norwegian National Cyber Security Centre
- The Australian Signals Directorate
- New Zealand’s certnz
- Netherland’s National Cyber Security Centre
- Israel’s National Cyber Directorate
- Agencies representing the governments of Japan, Singapore, and the Czech Republic
What is Security by Design?
CISA defines Security by Design as a development process “that reasonably protects against malicious cyber actors successfully gaining access to devices, data, and connected infrastructure.” In short, it requires teams to perform a risk assessment to anticipate threats and risks to a product or application, then build protections into the application as part of the normal development process.
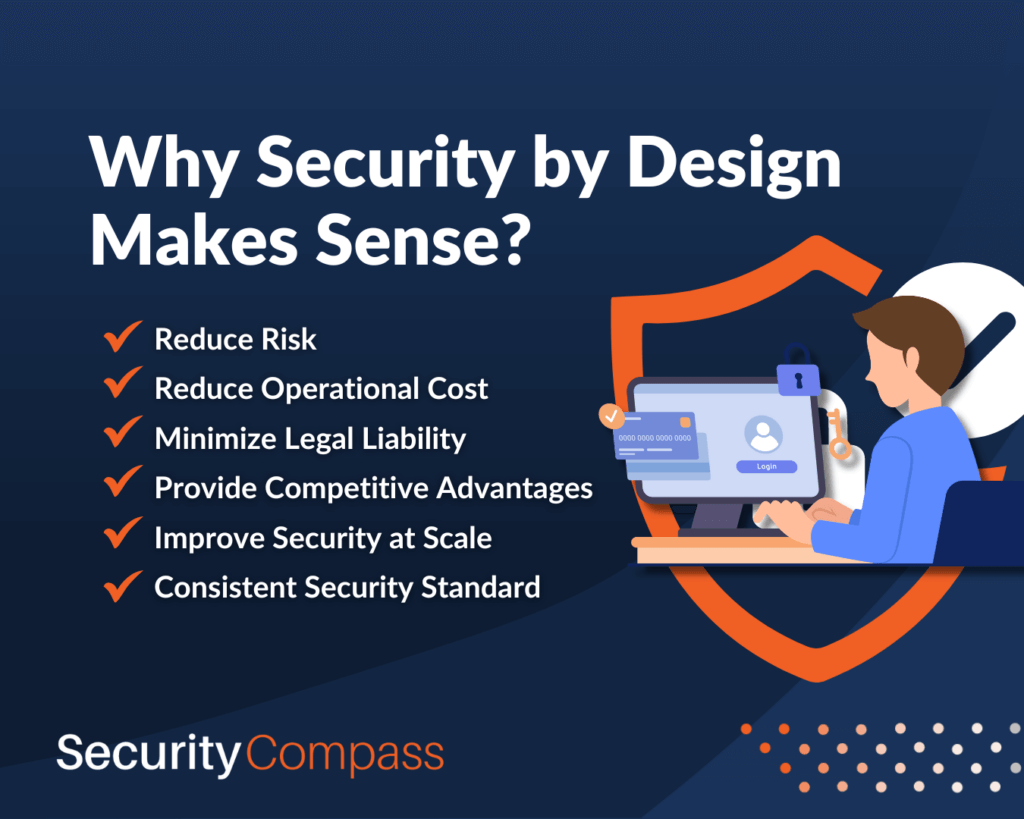
Why Security by Design Makes Sense
Building security into a software development process offers several benefits to organizations. Aside from simply protecting their own assets, a program that emphasizes building secure software can also:
- Reduce risk: Vulnerabilities found late in the development process are often added to “technical debt” due to perceived pressure to release new features. In other words, vulnerable software is shipped with the intent to address vulnerabilities in a subsequent release. Security by Design minimizes vulnerabilities by anticipating threats and risks.
- Reduce operational costs: While testing late in the development process will certainly uncover vulnerabilities, it comes at a high price. IBM (among others) has studied this and determined that a vulnerability discovered in system tests costs over 40 times more than if the bug was found and fixed during the design or coding phase. Those found in released software cost organizations over 600 times more!
- Minimize legal liability: The US government announced its National Cybersecurity Strategy. The strategy “seeks to build and enhance collaboration around five pillars.” Pillar 3 – “Shape Market Forces to Drive Security and Resilience” – is particularly important to organizations building software. Strategic objective 3.3 is to “…shift liability [for insecure software products and services] onto those entities that fail to take reasonable precautions to secure their software…” This is a significant shift. In the past, software users have borne the risk of vulnerabilities. This strategy turns that paradigm on its head. Jen Easterly, director of the Cybersecurity and Infrastructure Security Agency (CISA), took it further. During a speech in 2023, she stated, “…government can work to advance legislation to prevent technology manufacturers from disclaiming liability by contract…”
- Provide competitive advantages: A study by Prevalent found that 71 percent of organizations surveyed cited their top third-party risk as “a data breach or other security incident due to poor vendor security practices.” As concerns about supply chain security continue to grow, many organizations are conducting risk assessments of potential vendors and partners. Vendor risk assessments for software include reviewing an organization’s practices and controls to identify and mitigate risk from vulnerabilities, including physical security risks that could arise from poorly implemented software controls.
- Improve security at scale: Embedding security practices in the initial phases of application development allows development organizations to anticipate and address security issues at the design stage. By laying a secure foundation, organizations can scale their applications more confidently. As the application grows or evolves, the inherent security measures provide a stable and secure base for expansion, reducing risks associated with scaling.
- Consistent Security Standards: Security by design and secure coding guidelines encourage the establishment of consistent security standards and best practices across all phases of the development process. This consistency ensures that security threats and corresponding countermeasures are applied uniformly from project to project, reducing the risk of overlooking vulnerabilities.
Implementing Security by Design When Resources are Limited
While the shortage of security workers is real, there are strategies organizations can implement to compensate. Specifically, ongoing education and training can help shrink the skills gap by providing existing workforces with new security skills or in other cases by bridging the gap with the expansion of roles to better cover domains of application and product security. Training your development organization is certainly part of this strategy, however, we recommend going beyond foundational security training and having role-specific training for leaders who can help the organization achieve their security by design vision. When resources are limited, organizations should seek to optimize those who are already in key development roles with Security Champions training. This tactic can scale a security initiative by drawing in people without formal cybersecurity experience and giving them specific security training that builds on their key roles as the builder of good and secure code.
What is a Security Champion?
A Security Champion is an individual within an organization who acts as an advocate for security-related matters. They play a critical role in enhancing an organization’s Cyber security posture by bridging the gap between understaffed security teams and other departments or teams within the company.
Security Champions do not need to be senior development personnel. Those people already have multiple responsibilities. Likely candidates can include software engineers, testing, and software architects. The most critical criteria are involvement with the day-to-day development process and an understanding of the team’s goals, processes, and culture. As members of the technical team, Security Champions bridge the gap between the needs of security and the demands of business and engineering. They understand the need for quick-release cycles and can identify whether processes are effective or ineffective.
Security Champions are a Force Multiplier
Teams responsible for application security are dwarfed in size by development teams. The BSIMM 13 study by Synopsys analyzed 130 organizations and a total of over 400,000 developers managing over 145,000 applications. The average ratio of developers to Software Security Group members was 122:1. From an application standpoint, there was one Software Security Group member for every 43 applications!
Security Champions act as a force multiplier, extending the reach of security teams and promoting a security culture. They allow organizations to scale security and embed it within development teams. As developers first, they have a true understanding of the responsibilities of the development team and the requirement and pressures to ship functional software on time. Then, with their additional security training and investment in security as a priority and as another important feature of their end product, they are able to advocate for security requirements sooner and more consistently within the development cycle. When an organization has more people thinking about security as they do their jobs, they are likely to produce more secure software.
Making Security a Business Priority
Embedding Security Champions in the development team provides the developer organization with a stake in understanding and implementing security requirements instead of a “top-down” imposition of security requirements. Having Security Champions changes the developer experience and their interaction with security. It reduces organizational friction, changing the paradigm from meeting unknown security requirements to one where security is a shared business priority and teams have a common objective.
How to Build a Successful Security Champions Program
We have long advocated for Security by Design and Security Champions. Our work with clients has revealed six “markers of success” that distinguish successful programs that allow organizations to ship their applications with confidence when they secure software and applications by design:
1. Align on How You’ll Measure Success
Most successful organizations started their programs by assessing the security posture and maturity of their development teams as well as gaining agreement on the best security frameworks to follow. To set reasonable expectations, they also agreed on what Key Results they needed to achieve. These included the number of security champions trained, the number of security champions deployed, and the number of development teams with champions embedded. This allowed them to set appropriate goals and track progress over time.
2. Making Security Training “Sticky”
Learning is a process, not an event. Event-focused training, training by mandate, and other training pitfalls can backfire on an organization. We saw higher success when the development organizations were engaged with training material on a frequent basis. Material must be relevant to each individual’s role and responsibilities. Tailored learning paths that provide just enough relevant training can help prevent information overload and keep learners engaged. Contextual, Just-in-Time training that is embedded in security requirements tasks is best to support with reinforcement of security knowledge right when it’s needed.
3. Commitment to a Changed Culture
Security by Design and Security Champions require a change in culture. This can include security personnel sharing responsibilities they previously “owned.” To help break down barriers, one organization assigned eight cybersecurity experts for each area of expertise to act as mentors to the Security Champions. Another established a formal communication channel between Application Security, Security Champions, and Development teams to encourage exchanges. Leaders who align their objectives for security by design and communicate their progress against key security initiatives are communicating to the organization that they are committed to making a change in their approach and process.
4. Champions Among Peers
When only security and development leaders act as security champions, rank-and-file team members look at the program as being the responsibility of “management.” Culture change requires champions among peers. We found that organizations that adopted self-nominated Champions were able to better effect change. Seeing security advocates working shoulder to shoulder with the frontlines sustains what’s communicated top-down with execution from the bottom up.
5. Executive Sponsorship
Senior leadership support across departments is crucial to any successful program. This is particularly true when committing to Security by Design and Security Champions. Adopting these initiatives can include changed processes, responsibilities, and goals. We found that commitment to changing to a culture of security – including when this could delay a release – trickled down into commitment at every level of the organization. Having C-suite leaders affirm the value of security and its importance as a key company initiative goes a long way. This communicates the magnitude of security by design as a business requirement, not just a problem for security leaders to solve.
6. Include the Right Tools
People and processes are a big part of a successful program. However, the right technology allows processes to scale in a consistent and repeatable manner. Software manufacturers with mature security capabilities may turn to threat modeling tools to achieve their security by design vision. For example, our threat modeling and secure development platform, SD Elements, has been integral to our customers’ security by design journeys. It allows teams to automate threat modeling and create secure, compliant software by design. SD Elements provides teams with consistent and effective countermeasures at scale. These are automatically assigned to the appropriate personnel for implementation during appropriate phases of the normal development process. Supported by role-based Application Security Training, our customers have trained their developer workforce in security. They have also stood up Security Champions programs, which helped them put Security by Design into practice. Security Champions embedded within the development organization advocate for these security processes and support the scaling and adoption of Security by Design practices, especially when empowered with the right technology.
The Need for Security by Design
In today’s fast-paced and risk-laden digital landscape, embracing Security by Design is not just a recommendation; it’s a necessity. An organization that is educated in security by design and has embedded Security Champions will be better positioned to execute security by design principles all throughout the Software Development Life Cycle and foster a resilient and security-conscious culture across your teams.
Navigating this transformative journey requires expertise, strategic insight, and the right tools. This is where Security Compass steps in as your trusted partner. We’re not just advocates of Security by Design; we have pioneered security skills training and secure development tools that help you achieve it. We help you to confidently tackle security challenges head-on and secure your software by design and all throughout your development lifecycle.
Reach out to Security Compass today to chart your course toward a more secure digital future. Book a demo with us today and take the first step towards transforming your security landscape with Security by Design.