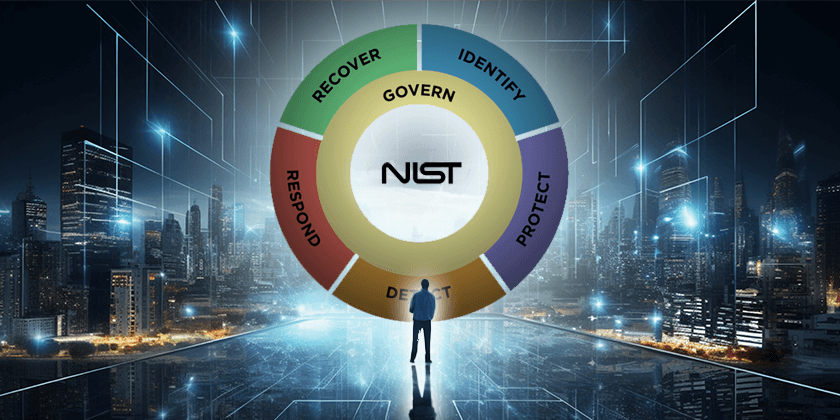
Unlocking the ROI of Security by Design in Application Development
In an era where digital threats evolve unprecedentedly, the traditional reactive stance on cybersecurity no longer suffices. Forward-thinking organizations are now embracing a proactive approach […]
Read More →