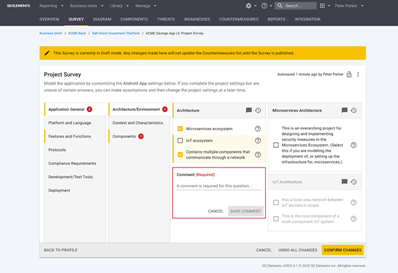
Mastering the 3E Framework: Elevating Your Security by Design Practices
In today’s digital landscape, the stakes for software security have never been higher. As cyber threats grow more sophisticated, the need for embedding security into […]
Read More →