Automating and Scaling Security in Software Development with SD Elements
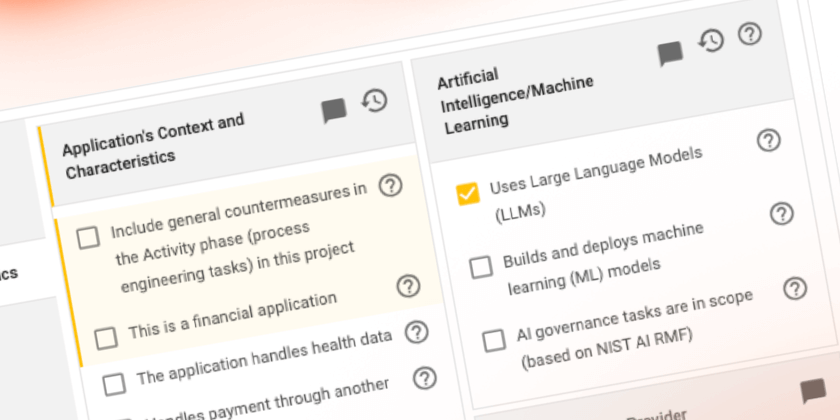
The rapidly evolving landscape of cybersecurity demands that organizations implement robust security measures and ensure that these measures are efficient and scalable. Tools like SD […]
Read More →